Setup a wireless mesh network with ubuntu laptops and olsrd
Setting up a wireless mesh network using ubuntu and olsrd.
Literature: http://www.viafrica.org/html/wireless.pdf
For viafrica.org I studied the possibility of setting up a wireless mesh network using ubuntu.
First some background on wireless networking.
You can have three different types of wireless layouts (“topologies”):
- a point to point network. Ideal when a fixed site does not have internet but
can “see” a side which has. The site with a dedicated internet connection
typically has a wireless Access Point (AP) configured. such an AP is usually
created using a dedicated device (like a linksys modem). This AP operates in
Master mode (sometimes called infrastructure mode). The site with no internet
normally has a wireless client which operates in Managed mode (sometimes called
client mode) and connects to the AP. - a point to multipoint network. This is the most commonly used. Multiple clients
(like laptops) operate in Managed mode to access a single AP (which operates in
Master mode). The clients can not communicate directly which each other,
traffic is always routed via the AP. - a multipoint to multipoint network, also called a mesh or ad-hoc network. To
create a mesh network all wireless nodes (like laptops) need to be put in
ad-hoc mode. In ad-hoc mode the nodes can communicate directly with each
other. This is the network I’ll explain in more detail.
The mesh nodes
All nodes in a mesh network need a fixed IP-address. To use DHCP (dynamically
assign IP-addresses) is not practical. A solution would be to use IPv6 only and
make use of the IPv6 stateless address autoconfiguration. With this technique
a unique IPv6-address is constructed using the MAC-address (MAC = Media Access
Control, a unique number for, in this case, each wireless card).
But for now we use fixed static IPv4 addresses.
I experimented with three PC’s:
- samsung laptop with:
- lucid desktop
- hostname: sammie
- eth0 (RJ-45) connection to the Internet (NATted by my linksys modem),
IP-address: 192.168.5.100 - atheros wireless card, will be configured with fixed IP-address 192.168.32.41
- madwifi wireless driver (compiled from source)
- asus eeePC 901 with:
- lucid desktop
- hostname: eeetje
- a Ralink RT2860 wireless card, will be configured with fixed IP-address
192.168.32.42 This card is quite famous:
https://bugs.launchpad.net/ubuntu/+source/linux/+bug/351362 To set this card
in ad-hoc mode was quite buggy, sometimes a command issued had effect and
sometimes it did not (…). However, once you get the card configured it stays
stable. - rt2860sta driver
- asus eee box pc with:
- lucid server
- hostname: eeebox
- atheros wireless card, will be configured with fixed IP-address 192.168.32.43
- ath9k driver
Configuring the nodes
Time to configure, starting with the samsung PC:
Login and be root. The lucid desktop network-manager is crap, stop it.
# /etc/init.d/network-manager stop
bring up the wireless interface
# ifconfig wlan0 up
Give the wireless adapter a network name (ESSID: Extended Service Set IDentifier),
Set the mode to “ad-hoc”
set the communication channel to 10
set RTS (“Request to Send”) to 250.
Because all nodes use the same channel you will have collisions on
the network. RTS can solve this a bit by negotiating if the line is clear.
(RTS uses “handshaking” for this).
Also allow fragmentation of packages
so to config the wireless adapter give the command:
# iwconfig wlan0 essid mesh mode ad-hoc channel 10 rts 250 frag 256
now it’s time to give the interface a IP-address
# ifconfig wlan0 192.168.32.41
the samsung laptop will act as a router to the Internet for the two eee pc’s
(eth0 is connected to the Internet).
Therefore issue:
# echo 1 > /proc/sys/net/ipv4/ip_forward
Because my laptop is already “NATted” by my linksys modem for my internet connection
on eth0, also route packets from 192.168.32.0 through NAT on eth0.
# iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
The result:
# iwconfig wlan0
wlan0 IEEE 802.11bg ESSID:"mesh"
Mode:Ad-Hoc Frequency:2.457 GHz Cell: 9E:87:AA:A7:0E:A0
Tx-Power=20 dBm
Retry long limit:7 RTS thr=250 B Fragment thr=256 B
Encryption key:off
Power Management:off
The Cell-value is constructed using the ESSID. Both the Cell-value and the ESSID must be the same
on the other nodes.
Now configure the asus eee PC 901:
the lucid desktop network-manager is still crap, stop it.
# /etc/init.d/network-manager stop
we do not need interface eth0 (RJ-45)
# ifconfig eth0 down
we do need our wireless interface
# ifconfig wlan0 up
If the device has a nickname remove it (the rt2860sta driver supports nicknames for the adapter)
# iwconfig wlan0 essid mesh nick "" mode ad-hoc channel 10 rts 250 frag 256
# ifconfig wlan0 192.168.32.42
configure your resolver. This was not needed on the samsung laptop because the resolver config
is not changed while eth0 is up. On the asus PC’s we do not use interface eth0.
# echo "nameserver 217.149.192.6" >> /etc/resolv.conf
# echo "nameserver 217.149.196.6" >> /etc/resolv.conf
As I said earlier the Ralink RT2860 wireless card is quite buggy to configure in ad-hoc mode.
Sometimes the above command iwconfig did not work but after hitting it again it did (…).
And sometimes you do not get the right Cell value. An “iwlist scan” did help me once (don’t
ask me why…).
Once configured the situation is stable.
I did the same for the eeebox pc (which does not have a network-manager because it’s a server install).
Use a routing daemon: olsrd
All three PC’s can now ping each other but we need “routing” to get the asus pc’s connected to
the internet.
For a few PC’s it is doable to edit the routing table by hand but if your network has a few more PC’s, and
even worse, PC’s come and go quite often, you want a routing daemon.
Especially for mesh networks is olsrd (optimized link state routing daemon) developed.
This daemon needs to run on every node and constantly polls it’s neighbours about
their status. Depending on the answers the network topology is reflected in the routing table.
To install on ubuntu just type:
# sudo apt-get install olsrd
The config file is /etc/olsrd/olsrd.conf. Copy this file to /etc (/etc/olsrd.conf is the default config file used by olsrd).
Most important in the config file is the section where you set your interface and the broadcast-address.
You need to set the broadcast-address the same on all mesh-nodes and 255.255.255.255 is used as a convention:
The olsrd.conf for both the asus eee PC’s contains:
Interface "wlan0"
{
Ip4Broadcast 255.255.255.255
}
The samsung laptop is a bit special because it’s a gateway to the internet for the asus PC’s.
To announce the fact it is a gateway to the other nodes is best done using a dedicated plugin.
To install olsrd plugins just type:
# sudo apt-get install olsrd-plugins
The plugin to annouce a node is a gateway is called olsrd_dyn_gw.so.0.4 and put in the config:
LoadPlugin "olsrd_dyn_gw.so.0.4"
{
# how often to check for Internet connectivity
# defaults to 5 secs
PlParam "Interval" "60"
PlParam "Ping" "217.149.194.145"
PlParam "Ping" "85.223.50.224"
}
You can also configure a gateway using HNA-syntax (Host and Network Association) but this method is now obsolete. HNA did not have capabilities to check if a host is really a gateway (for instance, if the internet connectivity is
suddenly gone the hosts keeps announcing it knows the way to the outside world).
This way you can create “black holes”. When using the plugin you avoid this by checking if the node still has
an internet connection (using ping to the configured IP-addresses) and make the proper announcements..
Once properly configured you can fire up olsrd by issuing (as root):
# olsrd -d 2
The option -d 2 puts the daemon in debug mode and it stays attached to your terminal so you can view the output. Once satisfied you can omit debug mode ans olsrd.
With the three nodes the debug output on, for instance the asus eee PC, will be:
*** olsr.org - 0.5.6-r7 (2009-11-24 03:49:26 on rothera) ***
--- 20:48:44.786334 ---------------------------------------------------- LINKSIP address hyst LQ ETX
192.168.32.42 0.000 0.976/0.945 1.084
192.168.32.41 0.000 0.965/0.945 1.097--- 20:48:44.786411 ----------------------- TWO-HOP NEIGHBORS
IP addr (2-hop) IP addr (1-hop) Total cost
192.168.32.42 192.168.32.41 2.097
192.168.32.41 192.168.32.42 2.084--- 20:48:44.786489 ------------------------------------------------- TOPOLOGY
Source IP addr Dest IP addr LQ ETX
192.168.32.41 192.168.32.42 1.000/1.000 1.000
192.168.32.41 192.168.32.43 0.945/0.949 1.115
192.168.32.42 192.168.32.41 1.000/1.000 1.000
192.168.32.42 192.168.32.43 0.945/0.965 1.097
192.168.32.43 192.168.32.41 0.949/0.937 1.124
192.168.32.43 192.168.32.42 0.976/0.945 1.084
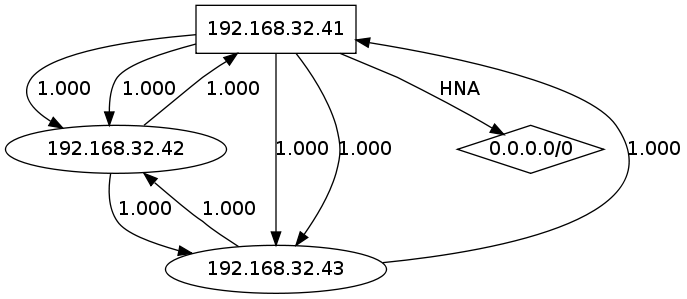
This is the output on 192.168.32.43
Clear is we know two other IP-addresses: 192.168.32.42 and 192.168.32.41
The hop to both IP-‘s use 1 hop.
The topology gives all 6 possible routes between the 3 nodes (3!).
The Link Quality (LQ) is for all links around 1.
The routing table before olsrd is started:
root@eeebox:~# netstat -rn
Kernel IP routing table
Destination Gateway Genmask Flags MSS Window irtt Iface
192.168.5.0 0.0.0.0 255.255.255.0 U 0 0 0 br0
192.168.32.0 0.0.0.0 255.255.255.0 U 0 0 0 wlan0
0.0.0.0 192.168.5.11 0.0.0.0 UG 0 0 0 br0
The routing table when all nodes have olsrd running:
root@eeebox:~# netstat -rn
Kernel IP routing table
Destination Gateway Genmask Flags MSS Window irtt Iface
192.168.32.41 0.0.0.0 255.255.255.255 UH 0 0 0 wlan0
192.168.32.42 0.0.0.0 255.255.255.255 UH 0 0 0 wlan0
192.168.5.0 0.0.0.0 255.255.255.0 U 0 0 0 br0
192.168.32.0 0.0.0.0 255.255.255.0 U 0 0 0 wlan0
0.0.0.0 192.168.32.41 0.0.0.0 UG 0 0 0 wlan0
0.0.0.0 192.168.5.11 0.0.0.0 UG 0 0 0 br0
Especially note the default gateway (to the samsung laptop (192.168.32.41)) is added.
A bit weird we have two default gateways now: the eeebox (192.168.32.43) also has a
RJ-45 connection to the linksys.
The route over wlan0 is surprisingly preferred (still has to investigate this).
A very neat plugin for olsrd is olsrd_dot_draw.so.0.3. This plugin starts a daemon on a port
you choose and outputs a “dot graph” (more info on the dot program see http://www.graphviz.org/) of the
current wireless topology.
Put in /etc/olsrd.conf:
LoadPlugin "olsrd_dot_draw.so.0.3"
{
PlParam "accept" "127.0.0.1"
PlParam "port" "2004"
}
This will start listening on localhost, port 2004.
A telnet to this port gives:
sammie:~$ telnet localhost 2004
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
digraph topology
{
"192.168.32.41" -> "192.168.32.42"[label="1.000", style=solid];
"192.168.32.41"[shape=box];
"192.168.32.41" -> "192.168.32.43"[label="1.000", style=solid];
"192.168.32.41"[shape=box];
"192.168.32.41" -> "192.168.32.42"[label="1.000"];
"192.168.32.41" -> "192.168.32.43"[label="1.000"];
"192.168.32.42" -> "192.168.32.41"[label="1.000"];
"192.168.32.42" -> "192.168.32.43"[label="1.000"];
"192.168.32.43" -> "192.168.32.41"[label="1.000"];
"192.168.32.43" -> "192.168.32.42"[label="1.000"];
"192.168.32.41" -> "0.0.0.0/0"[label="HNA"];
"0.0.0.0/0"[shape=diamond];
}
Connection closed by foreign host.
Copy the digraph output and save in topology.dot
Now use the dot program to graph this:
# dot -otopology.png -Tpng topology.dot
And voila: a real visualization of your mesh network topology!
Testing the mesh
Now the really important part: time to test the mesh. I take the eeePC (192.168.32.42) outside and see what happens.
The first node which could not be seen any more was the samsung laptop (192.168.32.41, the gateway…):
IP address hyst LQ ETX
192.168.32.41 0.000 0.698/0.039 INFINITE
192.168.32.43 0.000 0.871/0.110 10.461--- 20:31:07.295032 ----------------------- TWO-HOP NEIGHBORS
IP addr (2-hop) IP addr (1-hop) Total cost
192.168.32.43 192.168.32.41 INFINITE
192.168.32.41 192.168.32.43 11.465--- 20:31:07.295165 ------------------------------------------------- TOPOLOGY
Source IP addr Dest IP addr LQ ETX
192.168.32.41 192.168.32.43 1.000/1.000 1.000
192.168.32.42 192.168.32.43 0.871/0.110 10.461
192.168.32.43 192.168.32.41 1.000/1.000 1.000
192.168.32.43 192.168.32.42 0.102/0.251 39.078
Note the hop from .42 to .41 is gone and 192.168.32.41 has an ETX value of
“INFINITE”, which means that node is out of sight (unreachable).
But thanks to the mesh and olsrd we still have the eeebox pc (192.168.32.43) which routes us to the internet:
root@eeetje:~# traceroute -I 217.149.194.145
traceroute to 217.149.194.145 (217.149.194.145), 30 hops max, 60 byte packets
1 192.168.32.43 (192.168.32.43) 38.242 ms 71.653 ms *
2 * * *
3 * * *
4 * * *
5 * * *
6 * 10.254.3.22 (10.254.3.22) 9.889 ms 42.310 ms
7 * * *
8 * * *
9 * * *
10 * * *
11 * * *
12 colo.all-stars.nl (217.149.194.145) 200.526 ms 360.912 ms 393.447 ms
root@eeetje:~# ip route get !$
ip route get 217.149.194.145
217.149.194.145 via 192.168.32.43 dev wlan0 src 192.168.32.42
cache mtu 1500 advmss 1460 hoplimit 64
root@eeetje:~#
So it works! Quite nice actually 🙂
Some notes about a mesh network:
- performance can be a problem due to routing overhead and collisions. It’s clear that more
nodes add to this problem. - a mesh network can easily become quite complex and can make troubleshooting more difficult.
The complexity and variety of a mesh network can also make security hazardous.
Troubleshooting:
Wireless networking used to be crap, still is and probably will never improve much.
- sometimes it helps to enter the same command with iwconfig twice (…)
Especially with the Ralink wireless card. - sometimes it helps to bring wlan0 down and up again:
root@eeebox:~# ifconfig wlan0 down
root@eeebox:~# ifconfig wlan0 upNot sure yet but maybe has something to do with cached routing information (?)
- Sometimes you do not get the right Cell value. An “iwlist scan” did help me once (don’t
ask me why…).
Extending the mesh with a Linksys WAP54G
The WAP54G uses not much power (max 6 Watt) and can be used to extend our mesh.
The idea is to put it somewhere strategic in the mesh, may be even solar powered!
To get it to run olsr you need to put the “freifunk firmware” (see: http://wiki.freifunk.net/Freifunk_Firmware_%28English%29#WAP54G) on it.
My WAP54G is version 3.1 (with firmware 3.05, factory defaults).
What I did was:
- Connect a laptop to the LAN-poort in the same network (192.168.1.0/24).
- Go to http://192.168.1.245/fw-conf.asp and set “Downgrade Header” to “off”. This way you can download different firmware.
- Download the latest freifunk firmware from http://download.berlin.freifunk.net/ipkg/_trx/.
I got openwrt-freifunk-1.7.0-en.trx (I don’t know if the openwrt-freifunk-1.7.0-en-full.trx will fit). But the not full version has olsrd and you can always install more packages using “ipkg”. - Via the OLSR menu: set the IP4 broadcast to 255.255.255.255.
- Via the wireless menu” set a fixed wireless IP-address with 192.168.32.41 as the gateway (note: you should NOT use 192.168.0.0/16 IP-address for olsrd with freifunk firmware but I had no problems using 192.168.32.4X.). Furthermore set all the other values on the wireless-page: essid = mesh, mode = ad-hoc, channel = 10, RTS = 250, frag = 256.
- Via the LAN menu: don’t set a LAN default route (do NOT unset the IP-address or you can not connect anymore…!).
- Via the WAN-interface: disable the WAN interface (we use wireless for this :)).
- Choose “Restart”
That should do it. Login with ssh (username root, default password is admin (change this)) and see with
“ps ax | grep olsrd” if olsrd is running.
Now generate a new dot file (remember the telnet localhost localhost 2004 on host sammie?) and we start to have quite a mesh…:) :
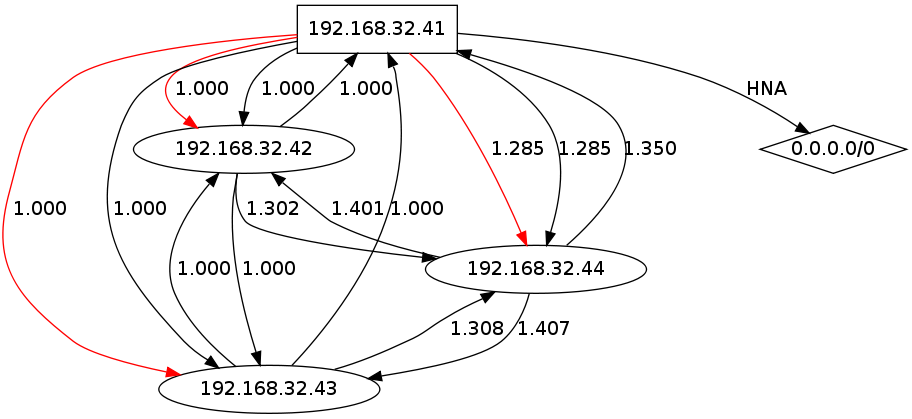
(I put the gateway announces from sammie (192.168.32.41) in red).
FYI: with ipkg-list you can see what packages are available:
alsa-lib - This is the library package for alsa, needed by some userspace programs.
alsa-utils - ALSA (Advanced Linux Sound Architecture) utilities
bluez-hcidump - Bluetooth packet analyzer
bluez-libs - Bluetooth library
bluez-utils - Bluetooth utilities
busybox-awk - Busybox awk,expr commands
busybox-coreutils - Busybox coreutils missing: cal, chgrp, chown, cmp, dirname,
busybox-crontab - Busybox crontab command
busybox-nc - Busybox nc (netcat) command
busybox-netstat - Busybox netstat command
busybox-nfsmount - Busybox mount command with NFS
busybox-ping6 - Busybox ping6 command
busybox-telnet - Busybox telnet command
busybox-tftp - Busybox tftp command
cipe-tap - Crypto IP Encapsulation (Tun version)
cipe-tun - Crypto IP Encapsulation (Tap version)
conntrack - Shows current internet connection activities in an overwiew.
dbus - Simple interprocess messaging system (daemon)
dropbear - Lightweight SSH client and server system
empcd - EMPCd can control the MPD
fakepop - POP3 server which delivers the same message to everyone
fftrace - A traceroute optimized of OLSR mesh networks
flite - Text-to-speech for embedded systems
freifunk-batman - B.A.T.M.A.N. (v0.2) suite for the FreifunkFirmware (FFF)
freifunk-berlin-mapaddon - Provides the old geopostions for the berlin mesh map
freifunk-bluetooth-de - Package for adding bluetooth dongle e.g. to wl500gP
freifunk-bluetooth-en - Package for adding bluetooth dongle e.g. to wl500gP
freifunk-dhcpsplash-de - DHCP-based captive portal (defaults from openwireless.ch)
freifunk-dhcpsplash-en - DHCP-based captive portal (defaults from openwireless.ch)
freifunk-dhcpsplash-pt - DHCP-based captive portal (defaults from openwireless.ch)
freifunk-dnsmasq - Provides customizations for freifunk webadmin
freifunk-dyndns-de - GUI for DynDNS
freifunk-dyndns-en - GUI for DynDNS
freifunk-dyndns-fr - GUI for DynDNS
freifunk-gateway-de - Internet gateway plugin for restricting the access to the
freifunk-gateway-en - Internet gateway plugin for restricting the access to the
freifunk-gateway-es - Internet gateway plugin for restricting the access to the
freifunk-gateway-fr - Internet gateway plugin for restricting the access to the
freifunk-iptables-missing - Missing iptables modules available in the original OpenWrt build.
freifunk-ipv6 - Package to run a parallel IPv6 instance of olsrd
freifunk-map-de - Map tool for freifunk firmware based on google maps
freifunk-map-en - Map tool for freifunk firmware based on google maps
freifunk-map-pt - Map tool for freifunk firmware based on google maps
freifunk-mtdkill - Call up mtd and kill init on return. (Note: Busybox
freifunk-netperf-de - Public Web-UI for netperf measurements.
freifunk-netperf-en - Public Web-UI for netperf measurements.
freifunk-netperf-fr - Public Web-UI for netperf measurements.
freifunk-nfsmount-de - This package can be used for NFS mounts. It will install
freifunk-nfsmount-en - This package can be used for NFS mounts. It will install
freifunk-nfsmount-es - This package can be used for NFS mounts. It will install
freifunk-nfsmount-fr - This package can be used for NFS mounts. It will install
freifunk-nvbackup-de - Backup-script to store local files/folders gzipped in nvram and restore after firmware-update
freifunk-olsr-viz-de - Visualization of OLSR Topology.
freifunk-olsr-viz-en - Visualization of OLSR Topology.
freifunk-olsr-viz-pt - Visualization of OLSR Topology.
freifunk-olsrd-libs - OLSR mesh networking daemon additonal libraries
freifunk-olsrd-old-libs - OLSR mesh networking daemon additonal libraries
freifunk-olsrd-old - OLSR mesh networking daemon for WRT54g for Freifunk.net
freifunk-olsrd - OLSR mesh networking daemon for WRT54g for Freifunk.net
freifunk-openvpn-de - Provides a GUI for OpenVPN
freifunk-openvpn-easyrsa-de - Provides a GUI for generating OpenVPN X.509 keys
freifunk-openvpn-easyrsa-en - Provides a GUI for generating OpenVPN X.509 keys
freifunk-openvpn-en - Provides a GUI for OpenVPN
freifunk-openvpn-nossl-de - Provides a GUI for OpenVPN
freifunk-openvpn-nossl-en - Provides a GUI for OpenVPN
freifunk-openwrt-compat - Some OpenWRT components are removed from the freifunk
freifunk-portfw-de - Provides Port Forwarding in Freifunk WebUI
freifunk-portfw-en - Provides Port Forwarding in Freifunk WebUI
freifunk-portfw-fr - Provides Port Forwarding in Freifunk WebUI
freifunk-pppoecd-de - Linksys PPPoE daemon for access to internet
freifunk-pppoecd-en - Linksys PPPoE daemon for access to internet
freifunk-pppoecd-es - Linksys PPPoE daemon for access to internet
freifunk-pppoecd-fr - Linksys PPPoE daemon for access to internet
freifunk-pppoecd-it - Linksys PPPoE daemon for access to internet
freifunk-pubpack-ca - This package can be used to publish own content
freifunk-pubpack-de - This package can be used to publish own content
freifunk-pubpack-en - This package can be used to publish own content
freifunk-pubpack-es - This package can be used to publish own content
freifunk-pubpack-fr - This package can be used to publish own content
freifunk-pubpack-it - This package can be used to publish own content
freifunk-pubpack-pl - This package can be used to publish own content
freifunk-pubpack-pt - This package can be used to publish own content
freifunk-qos-scripts-de - A simple administration interface for the openwrt qos-script package
freifunk-qos-scripts-en - A simple administration interface for the openwrt qos-script package
freifunk-radio - This package installs the necessary software and a start
freifunk-rdate - Provides customizations to set system time
freifunk-rdate - Provides customizations to set system time
freifunk-recommended-ca - This dummy package installs recommended software
freifunk-recommended-de - This dummy package installs recommended software
freifunk-recommended-en - This dummy package installs recommended software
freifunk-recommended-es - This dummy package installs recommended software
freifunk-recommended-fr - This dummy package installs recommended software
freifunk-recommended-it - This dummy package installs recommended software
freifunk-recommended-pl - This dummy package installs recommended software
freifunk-recommended-pt - This dummy package installs recommended software
freifunk-sdcard - Add the necessary kernel modules to drive
freifunk-sdinit - Additional tools to setup an sd/mmc card. Provides
freifunk-secureadmin-de - HTTPS for administrative tasks
freifunk-secureadmin-en - HTTPS for administrative tasks
freifunk-secureadmin-fr - HTTPS for administrative tasks
freifunk-secureadmin-pt - HTTPS for administrative tasks
freifunk-setbssid - Provides cgi-bin for setbssiding binary files with a browser
freifunk-statistics-de-le - Statistics package based on Round-Robin Database (RRD) collecting
freifunk-statistics-de - Statistics package based on Round-Robin Database (RRD) collecting.
freifunk-statistics-en - Statistics package based on Round-Robin Database (RRD) collecting.
freifunk-statistics-es - Statistics package based on Round-Robin Database (RRD) collecting.
freifunk-statistics-fr - Statistics package based on Round-Robin Database (RRD) collecting.
freifunk-tcpdump - Network traffic monitoring. This version
freifunk-topology-de - Shows the network topology of the neighborhood in the public webinterface
freifunk-upload - Provides cgi-bin for uploading binary files with a browser
freifunk-usbmobile - Installs necessary drivers for an usb device (e.g. mobile telephone)
freifunk-usbstick - Installs necessary drivers for an usb stick
freifunk-webadmin-0xff - Web UI for freifunk. Do not use standalone. This ipk
freifunk-webadmin-ca - Web UI for freifunk. Do not use standalone. This ipk
freifunk-webadmin-ch - Web UI for freifunk. Do not use standalone. This ipk
freifunk-webadmin-de - Web UI for freifunk. Do not use standalone. This ipk
freifunk-webadmin-en - Web UI for freifunk. Do not use standalone. This ipk
freifunk-webadmin-es - Web UI for freifunk. Do not use standalone. This ipk
freifunk-webadmin-ffgraz - Web UI for freifunk. Do not use standalone. This ipk
freifunk-webadmin-fr - Web UI for freifunk. Do not use standalone. This ipk
freifunk-webadmin-hsh - Web UI for freifunk. Do not use standalone. This ipk
freifunk-webadmin-it - Web UI for freifunk. Do not use standalone. This ipk
freifunk-webadmin-jawug - Web UI for freifunk. Do not use standalone. This ipk
freifunk-webadmin-ninux - Web UI for freifunk. Do not use standalone. This ipk
freifunk-webadmin-pl - Web UI for freifunk. Do not use standalone. This ipk
freifunk-webadmin-psf - Web UI for freifunk. Do not use standalone. This ipk
freifunk-webadmin-pt - Web UI for freifunk. Do not use standalone. This ipk
freifunk-webadmin-wlon - Web UI for freifunk. Do not use standalone. This ipk
freifunk-webadmin-wse - Web UI for freifunk. Do not use standalone. This ipk
freifunk-webif - Installs the webif variant from JCollake aka X-Win on Freifunk Minimal
freifunk-zapp-de - Shell script to check for filesharing on a
freifunk-zapp-en - Shell script to check for filesharing on a
gphoto2 - Gphoto Digital Camera Control
horst - Provides highly optimized radio scanning
hostapd-mini - This package contains a minimal IEEE 802.1x/WPA/EAP/RADIUS Authenticator
hostapd-utils - This package contains a command line utility to control the
hostapd - This package contains a full featured IEEE 802.1x/WPA/EAP/RADIUS
icecast - A streaming media server for Ogg/Vorbis and MP3 audio streams
id3lib - An ID3v1/ID3v2 tag manipulation library
inadyn - DynDNS client
ip6tables - The netfilter firewalling software for IPv6
ip - iproute2 stuff
iptables-extra - Other extra Iptables extensions (meta-package)
iptables-mod-conntrack - Iptables (IPv4) extensions for connection tracking
iptables-mod-extra - Other extra Iptables (IPv4) extensions
iptables-mod-filter - Iptables (IPv4) extension for packet content inspection
iptables-mod-imq - Iptables (IPv4) extensions for Intermediate Queuing Device QoS-support
iptables-mod-ipopt - Iptables (IPv4) extensions for matching/changing IP packet options
iptables-mod-ipsec - Iptables (IPv4) extensions for matching special IPsec packets
iptables-mod-nat - Iptables (IPv4) extensions for different NAT targets
iptables-mod-ulog - Iptables (IPv4) extension for user-space packet logging
iptables-utils - iptables-save and iptables-restore for Iptables (IPv4)
iptables - The netfilter firewalling software for IPv4
iptraf - shows network traffic
ircii - Internet Relay Chat Client
iwlib - Library for setting up WiFi cards using the Wireless Extension
kmod-audio - audio kernel module
kmod-bluetooth-bfusb - Bluetooth HCI BlueFRITZ! USB driver
kmod-bluetooth-bluecard - Bluetooth HCI BlueCard (PC Card) driver
kmod-bluetooth-bt3c - Bluetooth HCI BT3C (PC Card) drive
kmod-bluetooth-btuart - Bluetooth HCI UART (PC Card) driver.
kmod-bluetooth-dtl1 - Bluetooth HCI DTL1 (PC Card) driver
kmod-bluetooth-hciuart - Bluetooth HCI UART driver
kmod-bluetooth-hciusb - Bluetooth HCI USB driver
kmod-bluetooth-hcivhci - Bluetooth Virtual HCI device driver
kmod-bluetooth - Bluetooth stack kernel modules
kmod-firmware-class - firmware_class kernel module
kmod-gre - Kernel GRE tunneling support
kmod-imq - Kernel support for the Intermediate Queueing device
kmod-ip-conntrack-sip - ip_conntrack_sip kernel module
kmod-ip-nat-sip - ip_nat_sip kernel module
kmod-ip6tables - Kernel modules for ip6tables
kmod-ipt-conntrack - Extra Netfilter (IPv4) kernel modules for connection tracking
kmod-ipt-extra - Other extra Netfilter (IPv4) kernel modules
kmod-ipt-filter - Netfilter (IPv4) kernel modules for packet content inspection
kmod-ipt-ipopt - Netfilter (IPv4) kernel modules for matching/changing IP packet options
kmod-ipt-ipsec - Netfilter (IPv4) kernel modules for matching special IPsec packets
kmod-ipt-nat-default - Default Netfilter (IPv4) NAT kernel modules for special protocols
kmod-ipt-nat-extra - Extra Netfilter (IPv4) NAT kernel modules for special protocols
kmod-ipt-nat-h323 - Netfilter (IPv4) NAT kernel modules for H.323
kmod-ipt-nat-pptp - Netfilter (IPv4) NAT kernel modules for GRE and PPTP
kmod-ipt-nat-rtsp - Netfilter (IPv4) NAT kernel modules for RTSP
kmod-ipt-nat - Netfilter (IPv4) kernel modules for different NAT targets
kmod-ipt-queue - Netfilter (IPv4) kernel module for user-space packet queuing
kmod-ipt-ulog - Netfilter (IPv4) kernel module for user-space packet logging
kmod-iptables-extra - Extra kernel modules for iptables
kmod-ipv6 - ipv6 kernel module
kmod-madwifi - Driver for Atheros wifi cards, OpenWrt/Kamikaze version
kmod-mii - mii kernel module
kmod-openswan - Openswan IPSec kernel module
kmod-rt61 - Driver for Ralink RT2x61 PCI Wlan cards
kmod-rt73 - Driver for Ralink RT73 USB Wlan Sticks
kmod-sched - Kernel schedulers for IP traffic
kmod-soundcore - soundcore kernel module
kmod-tun - tun kernel module
kmod-usb-core - Kernel Support for USB
kmod-usb-ohci - Kernel driver for OHCI USB controllers
kmod-usb-storage - Kernel modules for USB storage support
kmod-usb-uhci - Kernel driver for UHCI USB controllers
kmod-usb2 - Kernel driver for USB2 controllers
kmod-usbnet - usbnet kernel module
kmod-vfat - Kernel modules for VFAT filesystem support
libao - A cross platform audio library
libaudiofile - Audio File library
libcurl - A client-side URL transfer utility
libdvbpsi4 - libdvbpsi is a simple library designed for decoding and
libexif - library for jpeg files with exif tags
libexpat - A fast, non-validating, stream-oriented XML parsing library.
libflac - Free Lossless Audio Codec library
libgcc - GCC support library
libgmp - GNU multiprecision arithmetic library
libgphoto2 - The basic library of the gphoto2 program.
libhowl - Zeroconf networking implementation (library)
libiconv - Character set conversion library
libid3tag - An ID3 tag manipulation library
libjpeg - The Independent JPEG Group's JPEG runtime library
libltdl - A generic dynamic object loading library
liblzo - LZO is a portable lossless data compression library written in
libmad - An high-quality MPEG audio decoding library
libncurses - a terminal handling library and common terminal definitions
libopenssl - OpenSSL libraries used for SSL encryption. Stripped down for use with OpenVPN
libosip2 - libosip2 is a library needed for SIP telephony
libpcap - a low-level packet capture library
libpcre - a Perl Compatible Regular Expression library
libpopt - a command line option parsing library
libpthread - POSIX threads library
librrd1 - Round Robin Database (RRD) management library.
libusb - A library for accessing Linux USB devices
libvorbisidec - A fixed-point Ogg/Vorbis decoder library
libxml2 - Gnome XML library
libxslt - Gnome XSLT library
madplay - MPEG audio player in fixed point
madwifi-tools - Driver utilities for Atheros 802.11a/b/g MiniPCI cards (openwrt.org/kamikaze)
mcast-test - Simple test programs for multicast routing
mgetty-nofax - Modem login program. This version with AUTO_PPP.
mgetty - Faxmodem suite. This version with AUTO_PPP, mgetty
micro-inetd - Simple network service spawner
micro-proxy - Really small HTTP/HTTPS proxy; Listens on port 3129
microcom - microcom is a minicom-like serial terminal emulator with scripting support.
motion - webcam motion sensing and logging
mpc - Music Player Daemon Console Client
mpd - Music Player Daemon
mrouted - Multicast routing daemon
mt-daapd - A multi-threaded DAAP (Digital Audio Access Protocol) daemon
mtrace - Multicast pendant of traceroute command
mystun - STUN server, build without SSL
nbd-server - Server to offer a network swap space
nbd - Client to use a network swap space
nc6 - Rewrite of netcat for IPv6 (from DeepSpace6)
netcat - Hobbits version of NetCat + Debian addons
netperfbin - Program and service to do network performance measurement.
nmap - Nmap is a free open source utility for network exploration or security auditing.
ntpclient - ntpclient is an NTP (RFC-1305) client for unix-alike computers.
olsrd - Standard OLSR daemon with normal debug and plugins
openssl-util - OpenSSL utitility command, required to manage X.509 keys
openswan - Openswan IPSec software
openvpn-nossl - OpenVPN is a full-featured SSL VPN solution which
openvpn - OpenVPN is a full-featured SSL VPN solution which
palantir - A multichannel interactive streaming solution
peercast - PeerCast is a fresh new P2P streaming server. It can stream music and
pimd - Multicast routing daemon for Protocol Idependant
pmacct - IP accounting tools (this package without nfacctd)
pppd - PPP daemon which implements the Point-to-Point
pppoecd - Linksys PPPoE daemon for access to internet using DSL modems
pptp - a Point-to-Point Tunneling Protocol (PPTP) client
pptpd - a Point-to-Point Tunneling Protocol (PPTP) server
qos-scripts - QoS module for OpenWrt
quagga-bgpd - A BGPv4, BGPv4+, BGPv4- routing engine for use with Quagga
quagga-isisd - An IS-IS routing engine for use with Quagga
quagga-ospf6d - An OSPFv3 routing engine for use with Quagga
quagga-ospfd - An OSPFv2 routing engine for use with Quagga
quagga-ripd - A RIP routing engine for use with Quagga
quagga-ripngd - A RIPNG routing engine for use with Quagga
quagga-vtysh - integrated shell for interacting with Quagga
quagga - A routing software package that provides TCP/IP
rexima - Sound Mixer
rrdcgi1 - Round Robin Database (RRD) CGI graphing tool.
rrdcollect - Round-Robin Database (RRD) collecting daemon
rrdtool1 - RRD is the Acronym for Round Robin Database. RRD is a system to store and display
rsync - utility that provides fast incremental file transfer
samba-client - NetBIOS/SMB simple client
samba-common - NetBIOS/SMB server and client shared files
samba-server - NetBIOS/SMB file and print server
siproxd - siproxd a SIP proxy daemon for VoIP
smstools3 - Receive/Send SMS via UMTS-USB-Stick
sox - Sox is a general purpose sound converter/player/recorder
srelay - socks 4/5 proxy
strace - A system call tracer
streamripper - streamripper
tc - iproute2 traffic control utility
tcpdump - A tool for network monitoring and data acquisition.
tftp-hpa - Server Daemon for TFTP/Bootp requests
tinc - TINC vpn daemon
uclibc++ - A standard c++ library for embedded systems
vls - VideoLan Streaming Server with Multicast
webif - A modular, extensible web interface for OpenWrt.
wificonf - Replacement utility for wlconf
wireless-tools - Tools for setting up WiFi cards using the Wireless Extension
wl-adv - Advanced version of the proprietary
wpa-supplicant - WPA Supplicant with support for WPA and WPA2
xrelayd - stunnel replacement based on xyssl
xyssl - Fast, open source implementation of SSL
zlib - Compression system used by many programs with overflow fix CAN-2005-2096